No matter how much you invest in cybersecurity products or cybersecurity consulting, your organization is likely to be attacked. This threat can take a small form, like a virus that can be easily eliminated, or a form too large to calculate, like a spear phishing attack that compromises the personal information of millions of customers. There is no cybersecurity product that can repel all kinds of cyber-attack at any given time. Therefore, when deciding which cybersecurity products you want to add to your cyber defense portfolio, it is essential to choose cybersecurity tools that can make your organization more flexible in responding to these threats. Cyber resilience means not only taking steps to stop threats, but also creating plans to minimize the potential impact of successful cyber attacks. A cyber resilience strategy is about ensuring that your business processes can continue uninterrupted and your data is protected from loss regardless of cyber incidents.
Together with our partners, we develop and provide effective products that your organization needs within the framework of a precise cyber resilience plan. We will evaluate turnkey solutions and products that meet the requirements of your organization and provide you with support throughout the necessary after-purchase phases of installation, integration, use, training, and technical support, bringing your organization to the cyber resilience and flexibility levels you need and desire.
Usorta Learning Management Platform
The Usorta Learning Management Platform was developed with the increasing demand for online and offline educational services during the pandemic in mind. On the Usorta Platform we serve both educational programs designed by our teams, as well as any other third party training programs. Tools required for such a Learning Management Platform such as image libraries, videos, interactive widgets, quizzes and surveys are easily usable for creating training material in Usorta.
Please click here to go to the SiberZincir Akademi web page, which utilizes the Usorta Platform.
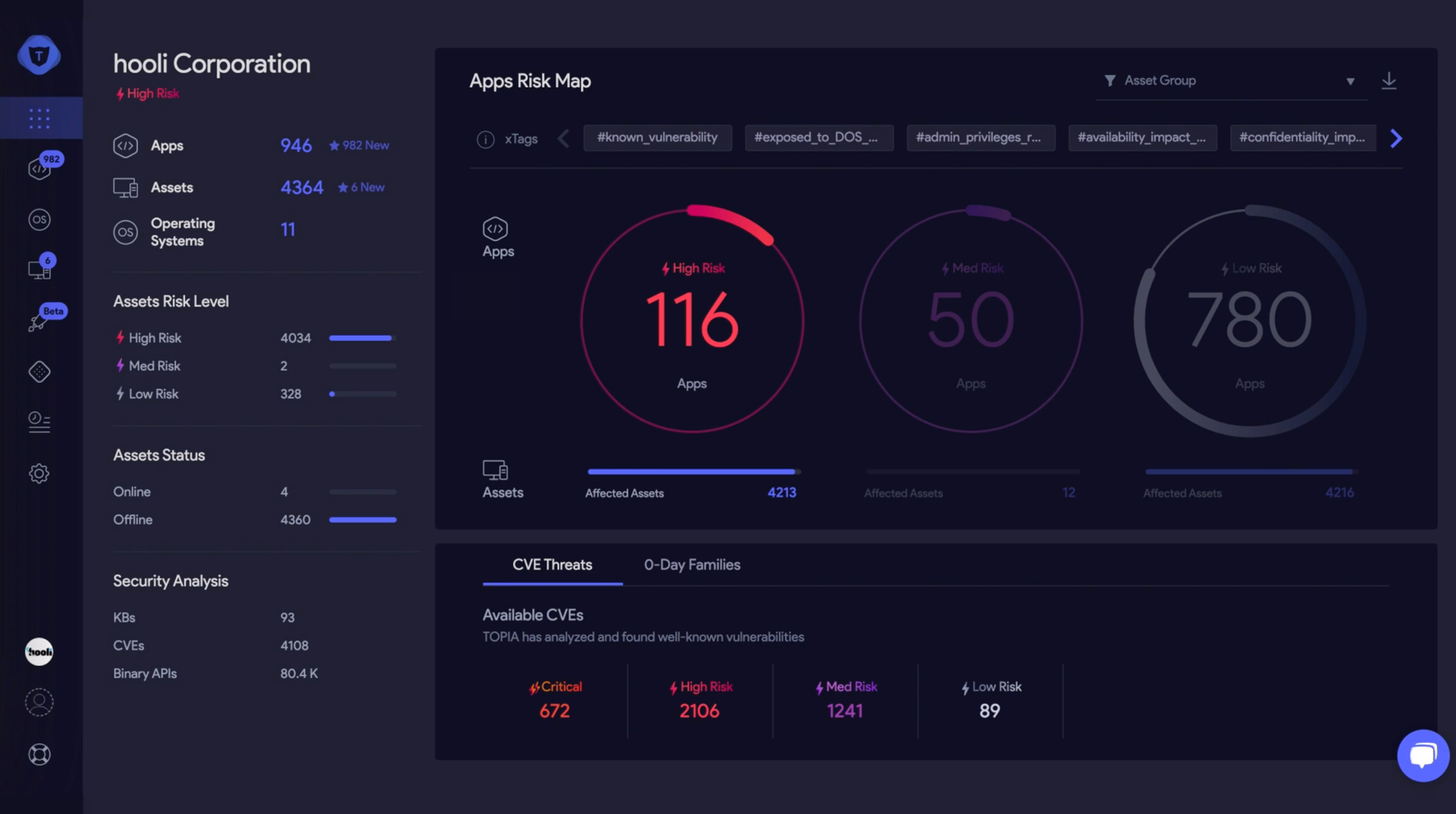
vRx
vRx provides all around protection for your installed operating systems and third-party software from critical vulnerabilities. Consolidate your software vulnerability assessment with vRx agent. vRx analyzes and assesses all applications for vulnerabilities, prioritizes according to your organization’s specific security posture, maps your digital environment, and recommends actions to help you eliminate potential risks and stay resilient. To help protect your organization from zero day threats, vRx’s 0-Day Analysis uses a proactive approach that continuously analyzes, predicts and identifies novel binary level threats. With effortless deployment and an easy-to-use interface, vRx is designed to be intuitive for anyone involved in your organization’s security cycle.
Please click here for the vRx brochure.
Please click here to go to the vRx web page.
DarkOwl
Darknet data is a proven driver of business success for use cases spanning beyond threat intelligence and investigations. DarkOwl API products allow cyber insurance underwriters and third party risk assessors to utilize discrete data points from the darknet and incorporate them into scalable business models that accelerate revenue growth.
DarkOwl’s superior darknet data breadth and depth improves the quality of your threat intelligence, enabling faster, more informed, darknet data-backed decision making.
MonSpark
Today, interruptions in websites can cause serious revenue losses, and content changes made by malicious actors can cause irreversible PR damage. MonSpark is a web application monitoring product that is used in more than 87 countries and has a correlation mechanism that detects interruptions, content changes and anomalies in websites, servers and applications.
Please click here to go to the MonSpark web page.
Malwation
Malwation specializes in malware research, sand-boxing and intelligence applications, and offers 3 distinct products:
Threat.Zone: Cloud-based malware sand-boxing and emulation platform. Threat.Zone aims to solve the common problems occurring around suspicious file analysis and malware hunting under one roof through various modules.
MSP: Allows users to create sophisticated malware with its simulation platform. With this capability, users can perform security validations of their own products and systems.
CDR: Decontamination technology that maximizes file security by performing Content Disarming and Reconstruction (CDR) on platforms and systems based on zero-trust architecture.
Please click here to go to the Malwation web page.
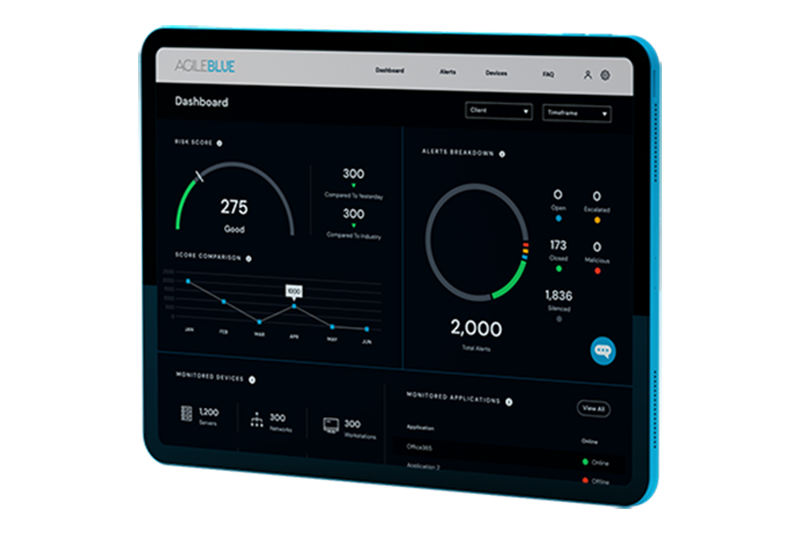
Agile Blue
Cloud-based SOC-as-a-Service platform. Using state-of-the-art methodologies such as Machine Learning, Automated Threat Monitoring, and Advanced Threat Detection, Agile Blue allows your organization to detect cybersecurity threats faster and more accurately. 24/7 monitoring, cloud security operations, data privacy and compliance needs are all covered for organizations where an internal SOC team is not feasible or affordable.
Please click here to go to the Agile Blue web page.
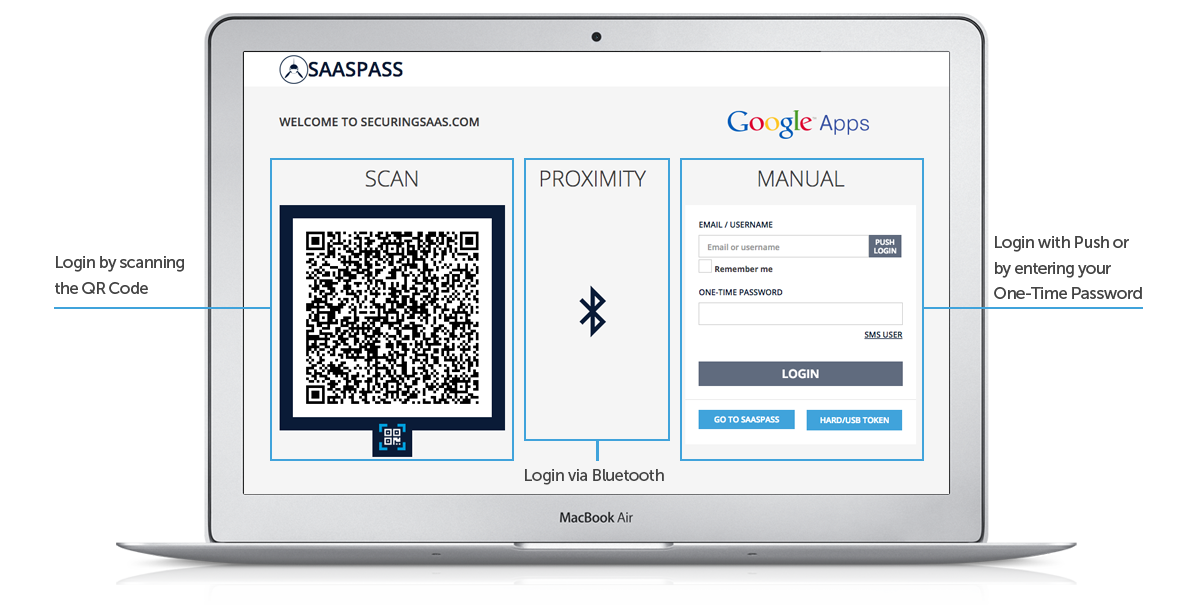
SAASPASS
Passwordless security solution. By providing a comprehensive and frictionless solution fully-secured with dynamic passcodes and multi-factor authentication, SAASPASS is the only identity and access management tool you need to secure your corporate network or your own personal data.
Please click here to go to the SaasPass web page.
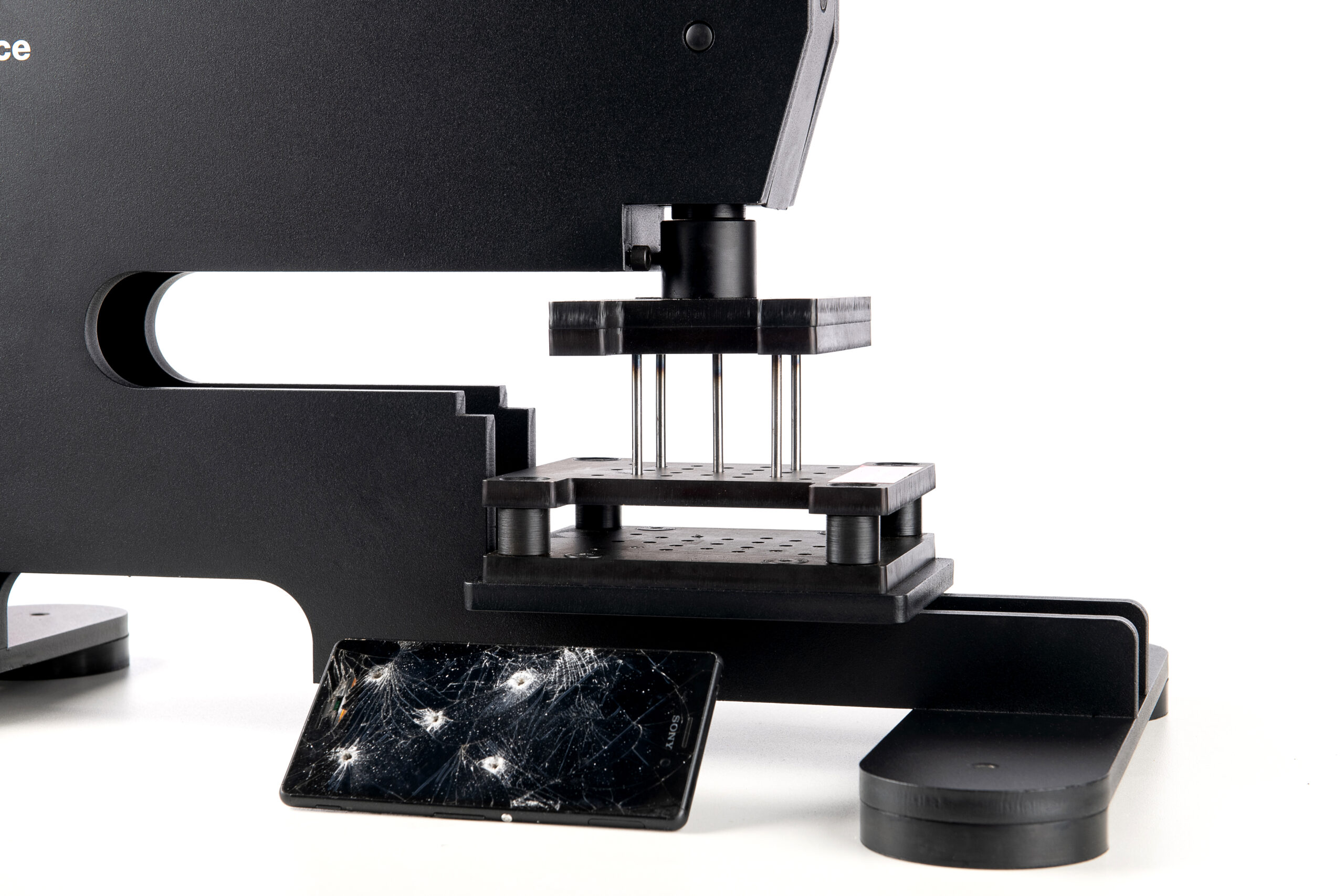
ProDevice
ProDevice is a global manufacturer of data destruction technologies, offering high-quality, innovative solutions for the safe and irreversible data removal from various types of storage media – degaussers and shredders/destroyers. On the data security side of requirements, ProDevice DSS (Drawer Storage System) cabinet is a perfect solution for secure storage of data carriers such as hard drives, magnetic tapes, disks, floppy disks, etc. Based on the extensive experience of ProDevice engineers, ProDevice supports companies in maintaining the highest security procedures for both removing and safekeeping information.
Please click here to go to the ProDevice web page.